Application white listing refers to the practice of specifying a guide of all the approved software applications which are permitted to be present as well as active on a computer system. The major goal of white listing is to protect the computers and all its networks from potentially harmful applications.
When it comes to the White List Approach, a white list is the key of approved entities. In fact, the National Institute of Standards and Technology suggests using Application Whitelisting Software in high-risk environments, where it is fundamentally important that the individual systems are secure and less important and the software’s can be useable without any restrictions. For more flexibility, a white list can also index approve the application components of software’s like libraries, extensions, plug-ins, and configuration files.
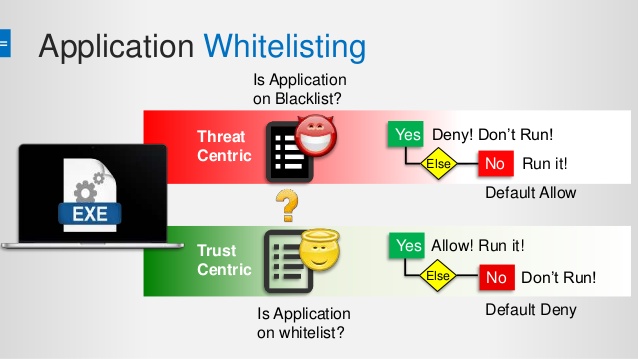
Application White listing Software vs. blacklisting
Unlike technologies that use application blacklisting that prevents the undesirable programs from executing; white listing is much more restrictive and also allows programming that has just been clearly permitted to run. There is no agreement among the security experts related to using which technique blacklisting or white listing or which is better. The proponents of blacklisting are complex as compared to white listing and can be difficult to manage. Also, maintaining the list that can be demanding due to the increase in the business applications and processes.
The Proponents of the White List Approach argue that it is not worth the time and effort which is needed to protect systems and prevent inappropriate programs from entering the network. Using a white list allows only applications that are approved of offers of more protection against malicious software.
How Application White listing Software works?
The implementation of application White listing Software begins with building a list of approved applications. The white list can be built into the host of the operating system, or it can also be provided by a third-party vendor. The simplest form of white listing allows the system administrator in specifying the file attributes that are associated with white listed applications like the file name, file size and the file path.
Microsoft has added Windows App locker to Windows Server 2008 R2 and Windows 7, that allows the system administration to specify which user and groups are permitted and which are not permitted.
Risks of using Application White listing Software
Attackers can replace white listed applications with spiteful apps with a relative ease that creates a version of their malware which is of the same size and also has the same file name as the permitted application, and further you can replace the white listed application with the spiteful one. Therefore, it is recommended and is much more effective for application to use white listing software to use cryptographic hashing techniques with digital signatures that have been linked with the software developers.
Promisec’s application white listing software is an essential tool for all those companies that want to keep their networks secure from unwanted applications and outside threats. If there is no file in your white list, then be it of any character, shape or size it cannot run.